Network Security Technology
A basic understanding of computer networks is requisite in order to understand the principles of network security. In this section, we’ll cover some of the foundations of computer networking, then move on to an overview of some popular networks. Following that, we’ll take a more in-depth look at TCP/IP, the network protocol suite that is used to run the Internet and many intranets.
Once we’ve covered this, we’ll go back and discuss some of the threats that managers and administrators of computer networks need to confront, and then some tools that can be used to reduce the exposure to the risks of network computing.

Definition Of Network:
A NETWORK has been defined as any set of interlinking lines resembling a net, a network of roads an interconnected system, a network of alliances. This definition suits our purpose well: a computer network is simply a system of interconnected computers. How they’re connected is irrelevant, and as we’ll soon see, there are a number of ways to do this.
1) The ISO/OSI Reference Model:-
The International Standards Organization (ISO) Open Systems Interconnect (OSI) Reference Model defines seven layers of communications types and the interfaces among them.
It isn’t important for you to memorize the ISO/OSI Reference Model’s layers, but it’s useful to know that they exist and that each layer cannot work without the services provided by the layer below it.
2) UUCP
UUCP (Unix-to-Unix CoPy) was originally developed to connect Unix hosts together. UUCP has since been ported to many different architectures, including PCs, Macs, Amigas, Apple IIs, VMS hosts, everything else you can name, and even some things you can’t. Additionally, a number of systems have been developed around the same principles as UUCP.

3) Internet
The Internet is the world’s largest network of networks. When you want to access the resources offered by the Internet, you don’t really connect to the Internet; you connect to a network that is eventually connected to the Internet backbone, a network of extremely fast network components. This is an important point: the Internet is a network of networks — not a network of hosts.

4) Domain Name System (DNS)
DNS stands for Domain Name System and is a distributed, replicated system that allows name servers to map domain names to an IP number. DNS is integral to the Internet in that it allows people to use hostnames rather than IP addresses (138.25.264.12) in web, e-mail, and other Internet protocols.
5) Router
A special-purpose computer or software package that handles the connection between 2 or more networks. Routers spend all their time looking at the destination addresses of the packets passing through them and deciding which route to send them on.
6) IP Address
IP has a number of very important features that make it an extremely robust and flexible protocol. For our purposes, though, we’re going to focus on the security of IP, or more specifically, the lack thereof. An I.P address is a 32-bit address fragmented in four parts each having an 8-bit address. There are mainly five classes of the I.P address.

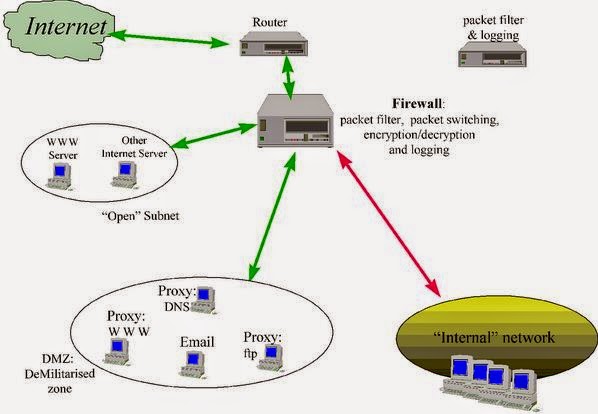
7) Firewalls
As we’ve seen in our discussion of the Internet and similar networks, connecting an organization to the Internet provides a two-way flow of traffic. This is clearly undesirable in many organizations, as proprietary information is often displayed freely within a corporate intranet (that is, a TCP/IP network, modeled after the Internet that only works within the organization).
In order to provide some level of separation between an organization’s intranet and the Internet, firewalls have been employed. A firewall is simply a group of components that collectively form a barrier between two networks. The pure definition of the firewall refers to the “A software or hardware or the combination of the software and hardware that filters all the incoming messages.